Master ASPM: Build a Security Shield
By: John Abhilash / May 20, 2024
Building a Security Fortress: Mastering Application Security Posture Management (ASPM) In today’s digital landscape, applications are the backbone of modern businesses. They store sensitive data, power critical operations, and connect us to customers. However, these applications are also prime targets for cyberattacks. This is where Application Security Posture Management (ASPM) steps in. ASPM provides a […]
Read More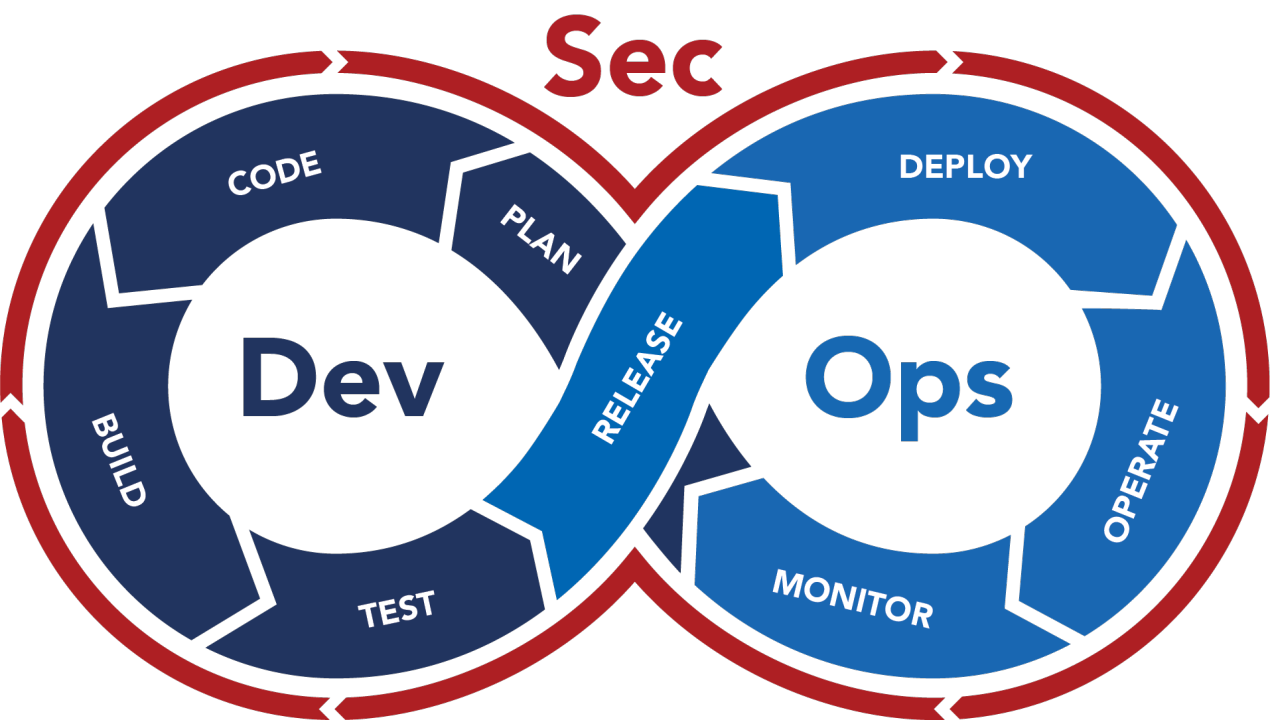
5 Continuous Phases of Sec in DevSecOps
By: John Abhilash / May 20, 2024
Building a Security Shield: The 5 Continuous Phases of Sec in DevSecOps DevSecOps, the marriage of development, security, and operations, has revolutionized software delivery. By integrating security throughout the development lifecycle, DevSecOps fosters faster deployments and more robust applications. However, security within DevSecOps isn’t a linear process; it’s a continuous loop of proactive measures. This […]
Read More
Master Your Logs with the ELK Stack
By: John Abhilash / April 8, 2024
The ELK Stack: A Powerful Open-Source Platform for Log Management and Analytics In the ever-expanding realm of IT infrastructure, maintaining visibility and control over vast quantities of log data is paramount. This is where the ELK Stack emerges as a shining star, empowering organizations to centralize, analyze, and visualize log data from diverse sources, […]
Read More
Revolutionize Your Business with DevSecOps: Unlocking Competitive Advantage
By: John Abhilash / April 4, 2024
Unlocking Competitive Advantage: How DevSecOps Can Revolutionize your Business In today’s fast-paced and ever-evolving digital landscape, businesses re constantly seeking ways to gain a competitive edge. One approach that has been gaining traction is DevSecOps – a powerful combination of development, security, and operations that can revolutionize the way companies function. By seamlessly integrating security […]
Read More
CASB Power Unleashed: Elevating Cybersecurity
By: John Abhilash / April 3, 2024
Unlocking the Power of CASB: Elevating Cybersecurity to New Heights In today’s digital landscape, cybersecurity has become a paramount concern for organizations of all sizes. With the ever-increasing sophistication of cyber threats, businesses need a robust solution that can safeguard their data and protect them from potential breaches. Enter CASB – Cloud Access Security […]
Read More
OWASP ZAP: The Ultimate Web Vulnerability Firewall
By: John Abhilash / April 3, 2024
In the ever-evolving realm of cybersecurity, staying ahead of threats requires a multi-layered approach. While firewalls and intrusion detection systems form the frontline defense, securing web applications demands a different kind of warrior – a web application security scanner. Enter OWASP ZAP, a free and open-source powerhouse that empowers developers, security professionals, and even beginners […]
Read More
Cloud Access Security Brokers: Your #1 Guide
By: John Abhilash / April 3, 2024
Demystifying the Cloud: Your Essential Guide to Cloud Access Security Brokers (CASBs) The cloud revolution has fundamentally transformed how businesses operate. From data storage and software applications to entire IT infrastructures, the cloud offers unparalleled scalability, agility, and cost-effectiveness. However, this shift to cloud-based resources introduces new security challenges. Traditional security perimeters built around physical […]
Read More
DevSecOps Encourages Creativity and Experimentation
By: John Abhilash / March 11, 2024
DevSecOps: Unleashing Creativity and Innovation Within a Secure Software Symphony In the fast-paced world of software development, innovation is the lifeblood. New features, functionalities, and technologies emerge at lightning speed, driven by the constant demand for a dynamic digital experience. However, this relentless pursuit of progress can sometimes clash with the vital […]
Read More
SonarQube vs Checkmarx:Ultimate Comparison
By: John Abhilash / March 11, 2024
SonarQube vs. Checkmarx: A Comprehensive Comparison of Code Quality and Security Scanning Tools for Informed Decision-Making In the ever-evolving world of software development, ensuring code quality and security has become a paramount concern. Two prominent tools that have gained significant traction in this domain are SonarQube and Checkmarx. Both tools offer robust […]
Read More
OWASP ZAP: Cyber Threat Defense Tips
By: John Abhilash / March 4, 2024
In today’s digital world, where cyber threats are constantly evolving, organizations face the critical challenge of securing their web applications and APIs. OWASP ZAP (Zed Attack Proxy) emerges as a powerful tool in this fight, empowering security professionals and developers to identify and address vulnerabilities before attackers exploit them. This article explores OWASP ZAP best […]
Read More