Assess Every Aspect of Your Applications
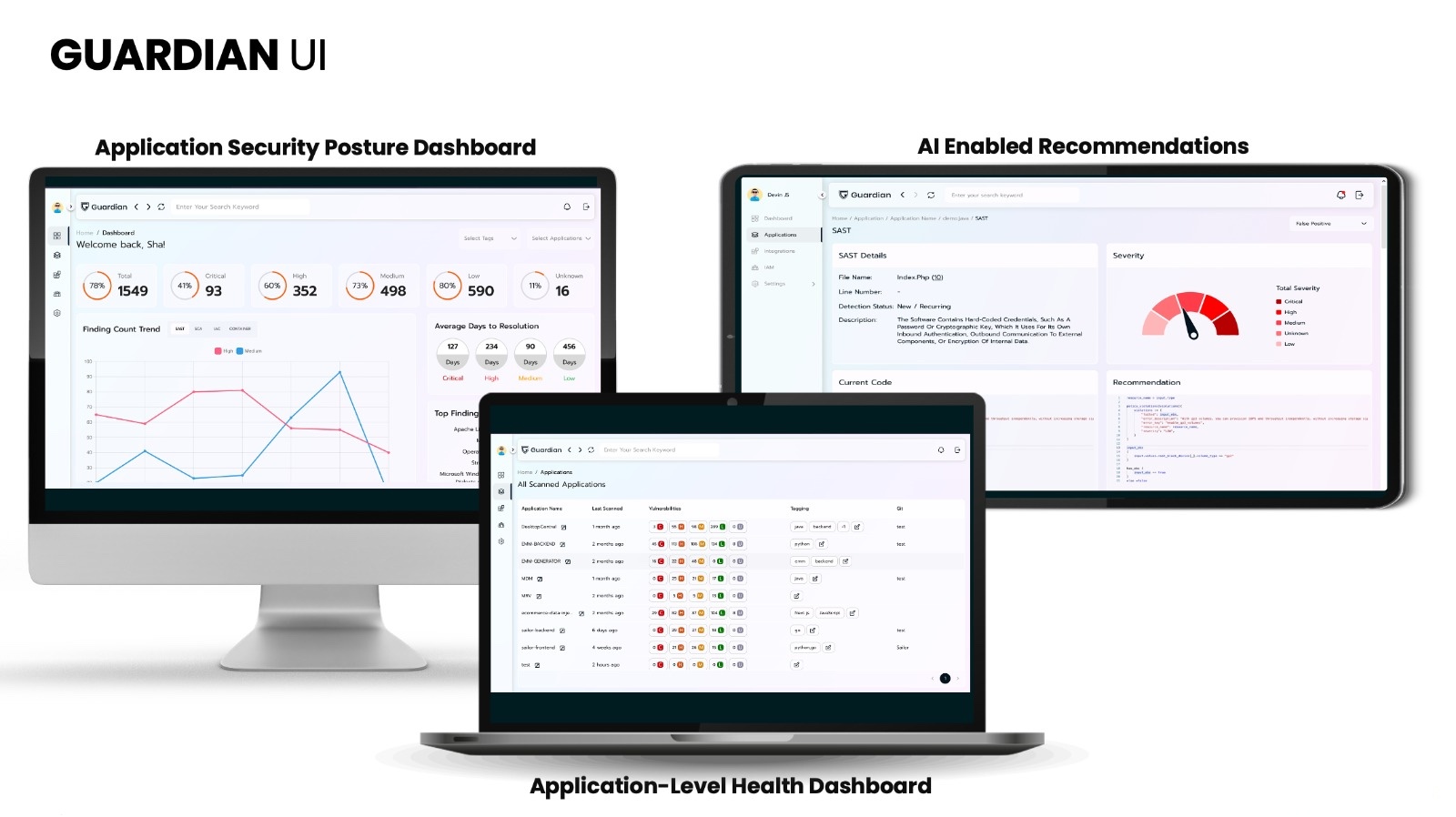
Securing web assets hinges on a thorough understanding of their existence. When organizations manage numerous web assets, they risk losing track of some, making them vulnerable to cyber threats.
Gain comprehensive visibility into all your applications, including those that may have been overlooked, forgotten, or intentionally hidden.
Conduct extensive scans across a wide range of web applications, web services, and web APIs, covering both first-party and third-party (open source) code. This process is independent of the technology, framework, or programming language used in their development.
Gain comprehensive visibility into all your applications, including those that may have been overlooked, forgotten, or intentionally hidden.
Conduct extensive scans across a wide range of web applications, web services, and web APIs, covering both first-party and third-party (open source) code. This process is independent of the technology, framework, or programming language used in their development.