 By: John Abhilash / June 18, 2024
By: John Abhilash / June 18, 2024
Enhancing Application Security with CI/CD Pipelines: A Comprehensive Technical Guide
In the rapidly evolving world of software development, Continuous Integration and Continuous Deployment (CI/CD) pipelines have become fundamental to maintaining efficiency and competitiveness. However, with the increasing speed and frequency of deployments, the risk of introducing security vulnerabilities also rises. This blog provides a detailed technical guide on integrating robust application security practices within your CI/CD pipeline to safeguard your software from threats while maintaining agility and innovation.
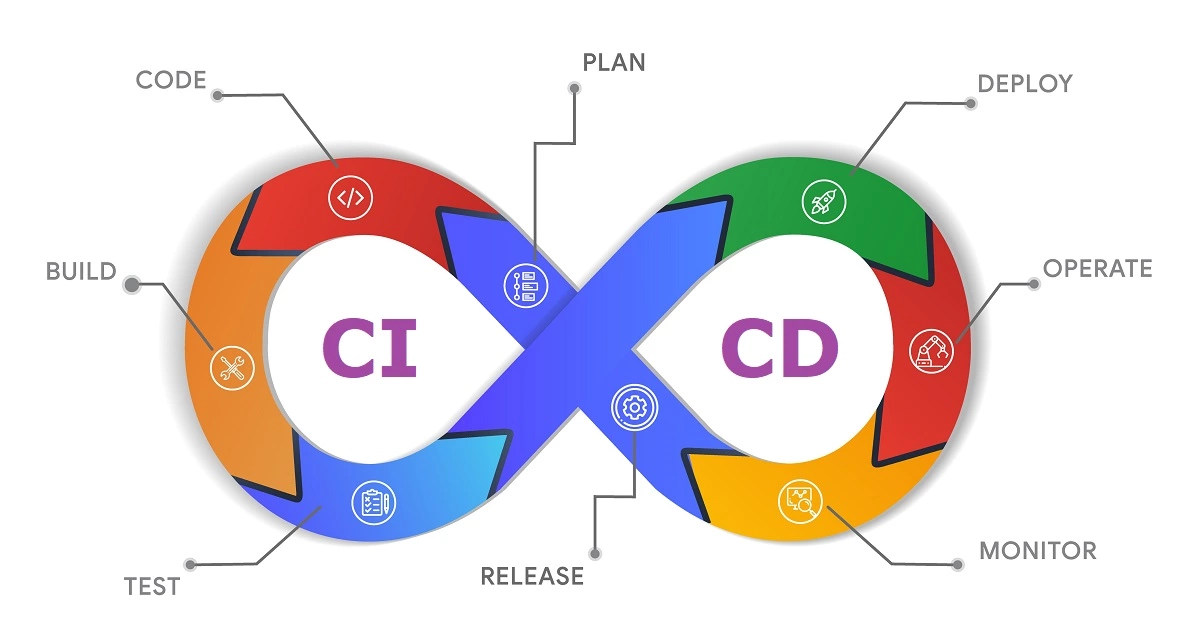
A CI/CD pipeline automates the process of integrating code changes, testing those changes, and deploying them to production environments. This automation allows development teams to deliver updates more frequently and reliably. The pipeline typically consists of several stages, including:
Source Code Management (SCM): Code is stored in a version control system like Git.
Continuous Integration (CI): Automated building and testing of code changes.
Continuous Deployment (CD): Automatic deployment of code to staging or production environments after passing tests.
Speed: Faster deployment cycles mean quicker delivery of features and bug fixes.
Reliability: Automated testing ensures that only quality code is deployed.
Efficiency: Reduces manual intervention, saving time and reducing human error.
Integrating security into CI/CD pipelines involves incorporating security practices and tools at every stage of the pipeline. This proactive approach helps identify and mitigate security vulnerabilities early in the development process.
The foundation of a secure CI/CD pipeline is secure source code management. This involves:
Automated Code Reviews: Use tools like GitHub Actions or Bitbucket Pipelines to automate code review processes. Automated linters and code analysis tools can catch basic issues before human review.
Manual Code Reviews: Implement a peer review process to ensure multiple sets of eyes inspect the code for potential security flaws.
Role-Based Access Control (RBAC): Implement RBAC to ensure only authorized personnel have access to the codebase.
Multi-Factor Authentication (MFA): Use MFA for accessing the version control system to add an extra layer of security.
Protected Branches: Set up protected branches that require code reviews and passing automated tests before merging.
Signed Commits: Enforce signed commits to verify the identity of commit authors.
During the CI stage, security practices focus on integrating security testing into the automated build and test processes.
SAST tools analyze the source code for security vulnerabilities without executing the code. These tools can identify issues such as:
SQL Injection: Detects vulnerabilities where SQL queries can be manipulated.
Cross-Site Scripting (XSS): Identifies places where user input is not properly sanitized.
Insecure Configurations: Finds configuration settings that may expose the application to risk.
Example Tools: SonarQube, Checkmarx, Fortify.
Modern applications often rely on third-party libraries and frameworks. Dependency scanning tools check these dependencies for known vulnerabilities.
Dependency Management: Tools like Dependabot and Renovate can automatically update dependencies to their latest secure versions.
Example Tools: OWASP Dependency-Check, Snyk, Black Duck.
During the CD stage, the focus shifts to ensuring that the deployment process itself is secure and that the deployed application is resilient against attacks.
DAST tools analyze the running application for security vulnerabilities by simulating attacks. This helps identify issues that might not be apparent from the source code alone.
Automated DAST: Integrate DAST tools into the CI/CD pipeline to run security tests on deployed staging environments.
Example Tools: OWASP ZAP, Burp Suite, Acunetix.
As infrastructure is increasingly managed as code, it’s crucial to ensure that this code is secure. IaC security tools scan your infrastructure definitions for vulnerabilities and misconfigurations.
IaC Scanning: Tools like Terraform Validator, TFLint, and Checkov can scan IaC templates for security issues.
Example Tools: Terraform, AWS CloudFormation, Ansible.
Even after deployment, security should remain a continuous concern. This involves monitoring the application and its environment for security issues and responding promptly.
RASP tools monitor the application in real-time, detecting and preventing attacks as they occur.
Real-Time Monitoring: Implement RASP solutions that can detect and block attacks in real-time.
Example Tools: Contrast Security, Signal Sciences.
SIEM systems collect and analyze security-related data from across your infrastructure, helping you detect and respond to security incidents.
Centralized Logging: Use tools like ELK Stack (Elasticsearch, Logstash, Kibana) or Splunk to aggregate and analyze logs.
Example Tools: Splunk, LogRhythm, IBM QRadar.
Regular Scans: Conduct regular vulnerability scans on your applications and infrastructure.
Patch Management: Ensure timely patching of vulnerabilities identified in scans.
Proactive Threat Modeling: Regularly conduct threat modeling sessions to identify potential security risks and design countermeasures.
Example Tools: Microsoft Threat Modeling Tool, OWASP Threat Dragon.
Developer Training: Regularly train developers on secure coding practices and the latest security threats.
Phishing Simulations: Conduct phishing simulations to educate employees on recognizing and avoiding phishing attacks.
Implementing security in a CI/CD pipeline requires a combination of tools, processes, and cultural shifts within the development team. Here are some best practices to help you get started:
Shift security left by integrating security practices early in the development lifecycle. This means involving security experts from the beginning and incorporating security checks in the initial stages of the CI/CD pipeline.
Security Gates: Implement security gates at each stage of the CI/CD pipeline to ensure security checks are passed before moving to the next stage.
Automation is key to ensuring that security checks are consistently applied without slowing down the development process. Integrate automated security testing tools in your CI/CD pipeline to catch vulnerabilities early.
Automated Testing Frameworks: Use frameworks like Jenkins, GitLab CI, and CircleCI to automate security tests.
Security doesn’t stop at deployment. Implement continuous monitoring to detect and respond to security threats in real-time. This includes using RASP, SIEM, and other monitoring tools.
Real-Time Alerts: Set up real-time alerts for any suspicious activities detected in the production environment.
Creating a culture that prioritizes security is crucial. This involves training developers on secure coding practices, promoting collaboration between development and security teams, and encouraging a proactive approach to security.
Security Champions: Appoint security champions within development teams to advocate for security best practices.
Ensure that all components of your application, including third-party libraries and frameworks, are regularly updated and patched to protect against known vulnerabilities.
Automated Patch Management: Use tools to automate the patch management process, ensuring timely updates.
Regular security audits and penetration testing can help identify and address security vulnerabilities that automated tools might miss. These tests simulate real-world attacks to evaluate the security posture of your application.
Red Team Exercises: Conduct red team exercises to simulate advanced persistent threats and test your incident response capabilities.
To illustrate the practical implementation of secure CI/CD pipelines, let’s consider a real-world example.
A fintech company wants to ensure the security of its CI/CD pipeline while maintaining rapid deployment cycles. Here’s how they implemented a secure CI/CD pipeline:
Source Code Management:
Implemented strict access controls and branch protection rules in GitHub.
Conducted regular code reviews with a focus on security.
Continuous Integration (CI):
Integrated SAST tools like SonarQube to scan the codebase for security vulnerabilities.
Used OWASP Dependency-Check to scan for vulnerabilities in third-party libraries.
Continuous Deployment (CD):
Deployed DAST tools like OWASP ZAP to analyze the running application for security issues.
Utilized Terraform for IaC, with regular scans for misconfigurations.
Post-Deployment Security:
Implemented RASP tools to monitor the application in real-time.
Used Splunk for centralized logging and SIEM to detect and respond to security incidents.
By integrating security into their CI/CD pipeline, the fintech company achieved the following outcomes:
Reduced Vulnerabilities: Early detection and remediation of security issues led to a significant reduction in vulnerabilities.
Increased Deployment Speed: Automation of security checks allowed for faster deployment cycles without compromising security.
Improved Compliance: Enhanced security practices helped the company meet regulatory requirements and industry standards.
Integrating security into your CI/CD pipeline is no longer optional—it’s a necessity in today’s threat landscape. By adopting a proactive approach to security, leveraging automated tools, and fostering a security-first culture, you can enhance the security of your applications without sacrificing speed and agility.
The key to successful implementation lies in understanding the specific security needs of your application and continuously evolving your security practices to address emerging threats. With a secure CI/CD pipeline, you can confidently deliver high-quality software that meets the highest standards of security.
By following the guidelines and best practices outlined in this blog, you can build a robust CI/CD pipeline that not only accelerates your development process but also fortifies your applications against security threats.
Key Features of Guardian:
1.Shift Left Security : Early Vulnerability Detection
2.Fast Track your VAPT: Gain insights to your application security posture across various assessments (SCA, SAST, DAST, IAC)
3.Security Driven Development : Streamlined Vulnerability Assessment and Penetration Testing(VAPT)
4.Integration with JIRA: Provided a centralized hub for tracking ,prioritizing and managing security issues.
5.AI powered Remediations: Immediate Resolution Guidance
Guardian’s AI delivers immediate resolution guidance upon identifying vulnerabilities, accelerating the remediation process and fostering a culture of proactive security to enhance overall code quality.
In an era where cybersecurity is paramount, Guardian serves as an indispensable ally, safeguarding applications throughout their lifecycle and empowering businesses to navigate the digital landscape with confidence.
Check Out our Other Resources: OpenTofu Vs Terraform

Leave a Comment