Is Your Security Incident Response Strategy Up to Par? Find Out Now!
By: John Abhilash / June 21, 2024
In today’s digital age, organizations are constantly at risk of cyberattacks and data breaches. An effective security incident response strategy is crucial for minimizing damage, reducing recovery time and costs, and preserving brand reputation. So, how robust is your security incident response strategy? Let’s delve into what makes a security incident response plan effective and […]
Read More
Unlock the Secrets to Effortless Compliance Management System!
By: John Abhilash / June 20, 2024
Navigating regulatory compliance demands more than understanding frameworks; it requires leveraging specialized tools within a robust Compliance Management System (CMS). This article explores key compliance frameworks like GDPR, HIPAA, PCI-DSS, SOX, and FISMA, examining their industry applications and detailing advanced tools designed to streamline compliance efforts. Ultimately, integrating these tools into a comprehensive compliance management […]
Read More
The Best Risk Assessment Tools for Fortifying Your Application Security
By: John Abhilash / June 19, 2024
Must-Have Risk Assessment Tool to Fortify Your Application Security! In today’s fast-paced digital world, the security of your applications is more critical than ever. With cyber threats constantly evolving, it’s essential to stay ahead by using the right risk assessment tool to protect your applications and infrastructure. As a CISO or senior leader in your […]
Read More
10 Must-Have Risk Assessment Tools for Your App Security!
By: John Abhilash / June 18, 2024
The Best Risk Assessment Tools for Fortifying Your Application SecuritySummaryVisibilityPublicPublishJune 18, 2024 9:34 am UTC+0TemplateDefault templateURLbootlabstech.com/risk-assessment-tools/Stick to the top of the blogAuthorGanga JhaHaritha GovindarajhellobltechJohn AbhilashMayank AwasthiMohan PSMohanlal SelvarajPrithik RoshanRaghul PrabuSamaya Ramesh SSara KamdodShakthi BalanSnekha PugalSoundharajan MahendranSwitch to draftMove to trashRevisions (82)CategoriesOthersUncategorizedAdd New CategoryTagsAdd New TagSeparate with commas or the Enter key.Featured imageCurrent image: Risk Assessment toolsReplaceRemoveExcerptWrite […]
Read More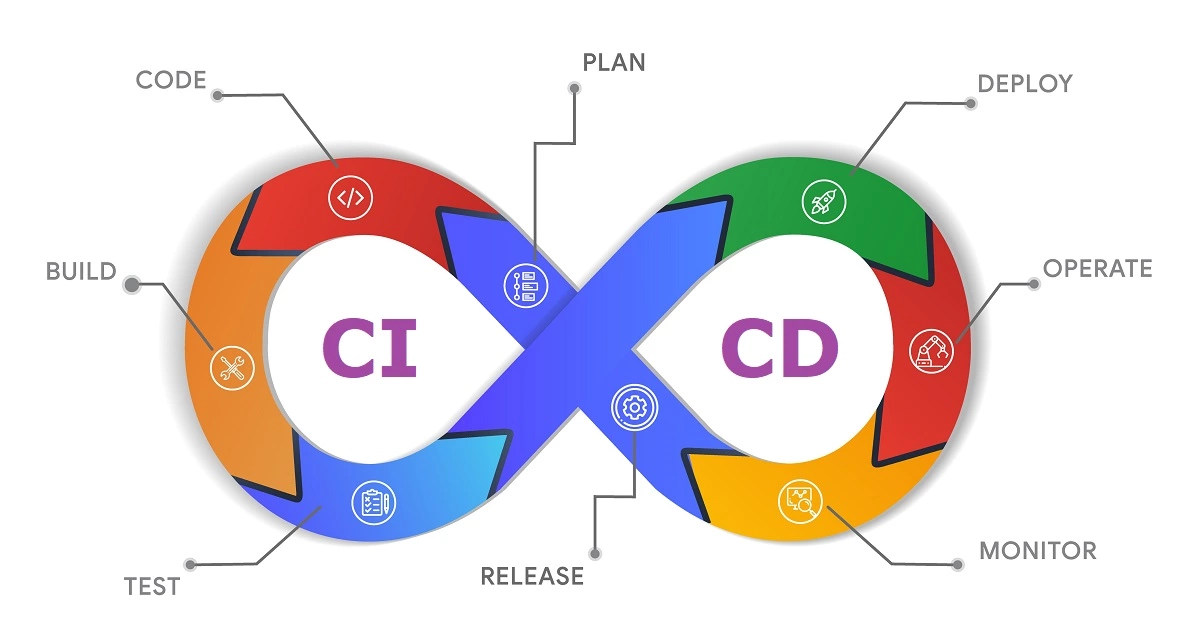
Securing Your Apps: A Technical Guide to CI/CD Pipelines
By: John Abhilash / June 18, 2024
Enhancing Application Security with CI/CD Pipelines: A Comprehensive Technical Guide In the rapidly evolving world of software development, Continuous Integration and Continuous Deployment (CI/CD) pipelines have become fundamental to maintaining efficiency and competitiveness. However, with the increasing speed and frequency of deployments, the risk of introducing security vulnerabilities also rises. This blog provides a […]
Read More
Web Application Firewalls (WAFs): A Deep Dive into Enhancing App Security
By: John Abhilash / June 17, 2024
Shielding the Digital Frontier: A Deep Dive into Web Application Firewalls (WAFs) for Enhanced App Security In the ever-evolving landscape of cybersecurity, web applications stand as prime targets for malicious actors. These applications, the engines driving our online experiences, hold a treasure trove of sensitive data – user credentials, financial information, and intellectual property. Breaches […]
Read More
SonarQube vs Checkmarx: A Side-by-Side Showdown
By: John Abhilash / May 29, 2024
Safeguarding Your Software: A Comparative Analysis of SonarQube vs Checkmarx In today’s software-driven world, security is no longer an afterthought; it’s an essential element of the development lifecycle. As applications become more complex and interconnected, the potential attack surface expands, making them vulnerable to various security threats. To combat these threats, developers and security professionals […]
Read More
Comprehensive Guide to Regression Testing: Safeguarding Stability
By: John Abhilash / May 28, 2024
Safeguarding Stability: A Comprehensive Guide to Regression testing In the ever-evolving world of software development, change is inevitable. New features are added, bugs are squashed, and code gets optimized. While these changes bring progress, they also introduce a potential risk: regressions. Regression testing emerges as a vital safeguard in this dynamic environment, ensuring that modifications […]
Read More
Mastering Risk Assessment for Cybersecurity Dominance
By: John Abhilash / May 27, 2024
Navigating the Digital Minefield: A Comprehensive Guide to Risk Assessment in Vulnerability Management The intricate web of an organization’s IT infrastructure is a treasure trove of sensitive data. However, this very value makes it a prime target for cyberattacks. In this ever-evolving digital landscape, where threats lurk around every corner, risk assessment becomes an essential […]
Read More
Ultimate Guide to Vulnerability Management Systems
By: John Abhilash / May 27, 2024
Shielding Your Organization: An Ultimate Guide to Vulnerability Management Systems In today’s ever-evolving digital landscape, cyber threats loom large. Malicious actors constantly seek to exploit weaknesses in computer systems and networks, putting sensitive data and critical infrastructure at risk. Here’s where vulnerability management systems (VMS) come to the forefront. This comprehensive guide delves into the […]
Read More