 By: John Abhilash / February 26, 2024
By: John Abhilash / February 26, 2024
Understanding CASB vs SASE :Which Solution is Right for your Business?
Are you trying to secure your business’s cloud data but unsure whether to go with a CASB or a SASE solution? We’ve got you covered. In this article, we’ll delve into the world of CASB (Cloud Access Security Broker) and SASE (Secure Access Service Edge) to help you understand their differences and determine which one is the right fit for your business.
CASB and SASE are both designed to enhance cloud security, but they approach it from different angles. CASB focuses on securing cloud applications and data by providing visibility, control, and threat protection. On the other hand, SASE takes a more holistic approach, encompassing not only cloud security but also secure connectivity and network transformation.
To make an informed decision, it’s important to understand the unique features and benefits of each solution. Both CASB and SASE have their strengths and weaknesses, and what works for one organization may not work for another. By the end of this article, you’ll have a clear understanding of CASB and SASE, enabling you to choose the solution that best aligns with your business objectives and security needs. So, let’s dive in and unravel the mysteries of CASB and SASE.
CASB, which stands for Cloud Access Security Broker, is a cloud security solution that acts as an intermediary between users and cloud service providers. It provides organizations with visibility into cloud usage, controls access to cloud resources, and protects sensitive data stored in the cloud.
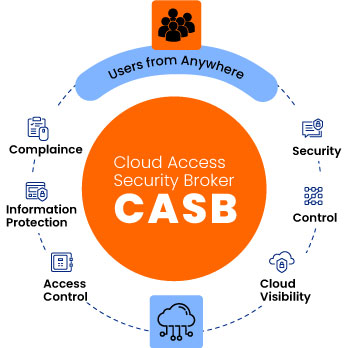
CASBs offer a wide range of features, including data loss prevention, threat protection, user behavior analytics, and encryption. These features help organizations prevent unauthorized access, detect and respond to security threats, and ensure compliance with industry regulations.
CASBs can be deployed in various ways, including as a standalone solution or integrated with existing security infrastructure. They can be deployed on-premises, in the cloud, or in a hybrid model. CASBs are typically used by organizations that want to secure their cloud applications and data while maintaining control over access and security policies.
CASBs provides various key features and benefits that help organizations improve their cloud security posture. Some of them are given below:
1. Visibility and control: CASBs offer visibility into cloud usage, allowing organizations to monitor and control user activities in the cloud. They provide insights into user behavior, including the use of unauthorized cloud applications and data sharing activities. With CASBs, organizations can enforce security policies, such as restricting access to certain cloud applications or blocking the sharing of sensitive data.
2. Data loss prevention: CASBs help prevent data loss by monitoring and controlling the flow of data to and from the cloud. They can detect and block the transmission of sensitive data, such as credit card numbers or social security numbers, to unauthorized recipients. CASBs also provide encryption capabilities to protect data at rest and in transit.
3. Threat protection: CASBs help organizations detect and respond to security threats in the cloud. They use advanced threat intelligence and machine learning algorithms to identify suspicious activities, such as unauthorized access attempts or data exfiltration. CASBs can also integrate with existing security solutions, such as SIEM (Security Information and Event Management) systems, to provide a comprehensive view of security events across the organization.
The benefits of using CASBs include improved visibility and control over cloud usage, reduced risk of data loss or breaches, simplified compliance management, and increased productivity by enabling secure cloud collaboration.
CASBs can be used in various scenarios to enhance cloud security. Here are some common use cases for CASBs:
1. Shadow IT discovery and control: CASBs can help organizations discover and control the use of unauthorized cloud applications (shadow IT). They provide visibility into cloud usage, allowing organizations to identify unauthorized applications and either block or approve them based on security policies.
2. Data protection and compliance: CASBs help organizations protect sensitive data stored in the cloud and ensure compliance with industry regulations. They provide data loss prevention capabilities, encryption, and policy enforcement to prevent unauthorized access or data sharing.
3. Threat detection and response: CASBs can detect and respond to security threats in the cloud, such as account compromise or malware infections. They use advanced threat intelligence and machine learning algorithms to identify suspicious activities and take appropriate actions, such as blocking access or generating alerts.
CASBs are suitable for organizations of all sizes and industries that use cloud applications and want to enhance their security posture and ensure compliance with industry regulations.
SASE, which stands for Secure Access Service Edge, is a cloud-native security framework that combines network security and wide-area networking (WAN) capabilities into a single unified solution. SASE is designed to address the security challenges of the modern digital workplace, where employees access applications and data from anywhere, using any device.
SASE brings together several security functions, including secure web gateways, firewall-as-a-service, zero-trust network access, data loss prevention, and secure web access. It provides organizations with a unified and scalable security architecture that can be applied consistently across all network edges.
SASE is based on the principles of zero trust, which means that all users, devices, and applications are treated as untrusted and must be verified and authorized before accessing corporate resources. This approach helps organizations reduce the attack surface and minimize the risk of data breaches.
SASE offers several key features and benefits that make it an attractive solution for organizations looking to enhance their cloud security and network connectivity.
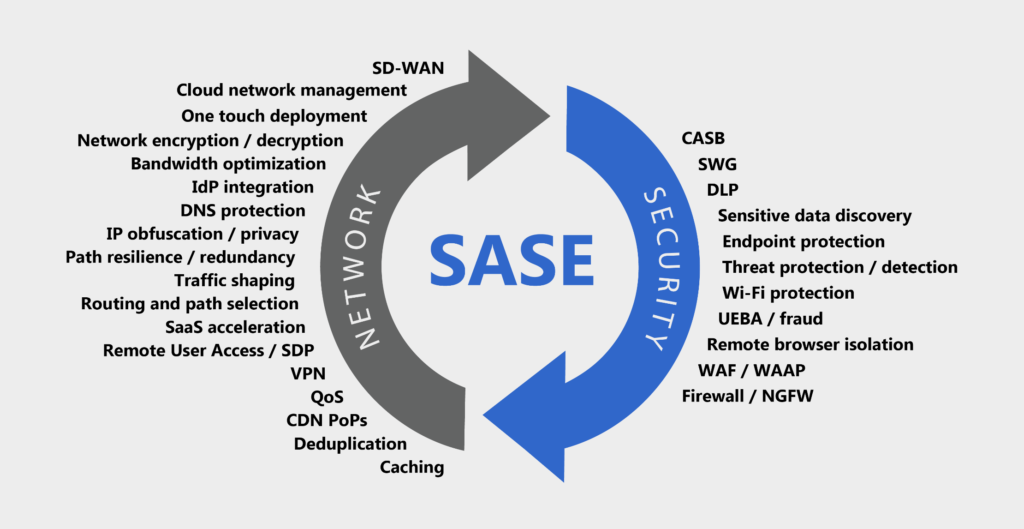
1. Secure connectivity: SASE provides secure and reliable connectivity for remote workers, branch offices, and cloud resources. It combines software-defined wide-area networking (SD-WAN) capabilities with secure web gateways to optimize network performance and ensure the secure transmission of data.
2. Zero-trust network access: SASE implements the zero-trust security model, which ensures that all users and devices are authenticated and authorized before accessing corporate resources. This approach minimizes the risk of unauthorized access and helps organizations enforce security policies consistently across all network edges.
3. Integrated security services: SASE integrates multiple security services, such as firewall-as-a-service, data loss prevention, and secure web access, into a single unified solution. This eliminates the need for multiple point solutions and simplifies security management.
The benefits of using SASE include improved network performance and reliability, enhanced security posture, simplified management and deployment, and reduced costs by eliminating the need for multiple security solutions.
SASE can be used in various scenarios to address the security and networking needs of modern organizations. Here are some common use cases for SASE:
1. Secure remote access: SASE provides secure remote access for employees working from home or on the go. It ensures that all remote connections are authenticated and encrypted, protecting sensitive data from unauthorized access.
2. Branch office connectivity: SASE enables secure connectivity for branch offices, eliminating the need for expensive MPLS (Multiprotocol Label Switching) networks. It optimizes network performance and ensures the secure transmission of data between the headquarters and branch offices.
3. Cloud security: SASE helps organizations secure their cloud resources by providing integrated security services, such as firewall-as-a-service and data loss prevention. It ensures that all cloud connections are secure and compliant with organizational security policies.
SASE is suitable for organizations that have a distributed workforce, use cloud applications and resources, and want to simplify their security and networking infrastructure.
Now that we have a clear understanding of CASB and SASE, let’s compare their features and capabilities to help you make an informed decision.
| Feature | CASB | SASE |
|---|---|---|
| Focus | Securing cloud applications and data | Securing cloud, connectivity, network |
| Visibility and Control | Granular control over cloud usage | Control over network traffic and user access |
| Data Loss Prevention | Specialized in data loss prevention | Offers data loss prevention capabilities |
| Secure Connectivity | Provides secure connectivity to some extent | Optimizes and secures network connectivity |
| Integration | Can be integrated with existing security infrastructure | Integrates multiple security services into a unified solution |
| Scalability | Can scale, may require additional hardware or software deployment | Leverages cloud-native architectures and software-defined networking for scalability |
When choosing between CASB and SASE, there are several factors to consider:
| Factor | Consideration for CASB | Consideration for SASE |
|---|---|---|
| Business Objectives | Ideal for securing cloud applications and data | Suitable for optimizing network connectivity and enhancing remote access |
| Cloud Adoption | Well-suited for organizations heavily invested in cloud applications | More appropriate for organizations with distributed workforces and multiple branch offices |
| Budget and Resources | May require additional hardware or software deployment | Leverages cloud-native architectures, reducing upfront investments |
| Integration Capabilities | Can integrate with existing security infrastructure, such as SIEM systems | Provides integrated security services out of the box |
| Vendor Expertise and Support | Assess vendor expertise and support provided | Look for vendors with a track record of delivering quality solutions and excellent customer support |
Conclusion: Choosing the right solution for your business?
In conclusion, CASB and SASE are two distinct solutions that offer different approaches to enhancing cloud security. CASB focuses on securing cloud applications and data, while SASE takes a holistic approach, encompassing secure connectivity and network transformation.
To choose the right solution for your business, consider your specific security and networking needs, cloud adoption strategy, budget, integration capabilities, and vendor expertise. Both CASB and SASE have their strengths and weaknesses, and what works for one organization may not work for another.
By understanding the unique features and benefits of CASB and SASE, you can make an informed decision that best aligns with your business objectives and security needs. Whether you choose CASB to secure your cloud applications and data or opt for SASE to enhance your network connectivity, both solutions can significantly improve your organization’s overall security posture in the cloud era. So, take the time to evaluate your options and make a decision that will help safeguard your business’s critical assets in today’s ever-evolving threat landscape.
Remember, the security of your business’s cloud data is of utmost importance, and choosing the right solution is a crucial step towards ensuring its protection. So, don’t rush the decision. Take the time to assess your needs and select the solution that best fits your organization. With the right solution in place, you can confidently embrace the cloud and leverage its advantages while keeping your data safe and secure.
Guardian: Revolutionizing Application Security
Key Features of Guardian:
1.Shift Left Security : Early Vulnerability Detection
2.Fast Track your VAPT: Gain insights to your application security posture across various assessments (SCA, SAST, DAST, IAC)
3.Security Driven Development : Streamlined Vulnerability Assessment and Penetration Testing(VAPT)
4.Integration with JIRA: Provided a centralized hub for tracking ,prioritizing and managing security issues.
5.AI powered Remediations: Immediate Resolution Guidance
Guardian’s AI delivers immediate resolution guidance upon identifying vulnerabilities, accelerating the remediation process and fostering a culture of proactive security to enhance overall code quality.
In an era where cybersecurity is paramount, Guardian serves as an indispensable ally, safeguarding applications throughout their lifecycle and empowering businesses to navigate the digital landscape with confidence.
Check Out our Other Resources: OpenTofu Vs Terraform

Leave a Comment