We are continuous experimenters in DevSecOps transformations. Having successfully transformed large digital platforms across various industries including Automotive, BFSI & Retail, e-commerce, our motto is to engineer a seamless digital fluency to your business. Powered by DevSecOps tools of your choice, this package delivers in just 3-6 months, your automation needs. For beginners, intermediates and advanced SaaS organizations.
Approaches:
DevSecOps is an approach that integrates security practices into the DevOps (Development and Operations) process, ensuring that security is an inherent part of software development. Here’s a comprehensive DevSecOps approach:
![]() Shift-Left Security:
Shift-Left Security:
Start security considerations early in the development process, from design to coding.
![]() Security Training:
Security Training:
Train and educate development and operations teams on security best practices.
![]() Threat Modeling:
Threat Modeling:
Conduct threat modeling to identify vulnerabilities and prioritize security efforts.
![]() Security Automation:
Security Automation:
Automate security testing, including Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST).
![]() Code Analysis:
Code Analysis:
Regularly review code for security issues and use automated tools to identify vulnerabilities.
![]() Vulnerability Management:
Vulnerability Management:
Establish a process to identify, prioritize, and remediate security vulnerabilities.
![]() Continuous Integration/Continuous Deployment (CI/CD):
Continuous Integration/Continuous Deployment (CI/CD):
Implement security checks and tests in CI/CD pipelines for early detection and prevention.
![]() Container Security:
Container Security:
Secure containers by scanning container images for vulnerabilities and enforcing security policies.
![]() Configuration Management:
Configuration Management:
Ensure secure configurations for infrastructure and applications to prevent misconfigurations.
![]() Identity and Access Management (IAM):
Identity and Access Management (IAM):
– Implement strong authentication and authorization mechanisms to control access.
![]() Monitoring and Logging:
Monitoring and Logging:
– Continuously monitor for security threats and maintain detailed logs for analysis.
![]() Incident Response Plan:
Incident Response Plan:
– Develop a robust incident response plan and regularly test it to handle security breaches.
![]() Compliance and Auditing:
Compliance and Auditing:
– Ensure that the application complies with industry-specific regulations and standards. Conduct regular security audits.
![]() Secure Cloud Practices:
Secure Cloud Practices:
– Follow security best practices for cloud services and infrastructure, leveraging cloud-native security features.
![]() Collaboration:
Collaboration:
– Foster a collaborative culture where development, operations, and security teams work together seamlessly.
![]() Culture and Awareness:
Culture and Awareness:
– Cultivate a security-aware culture, encouraging communication about security issues and lessons learned.
![]() Continuous Improvement:
Continuous Improvement:
– Regularly assess and update security measures to adapt to new threats and technologies.
![]() Knowledge Sharing:
Knowledge Sharing:
– Encourage knowledge sharing and learning from security incidents and challenges.

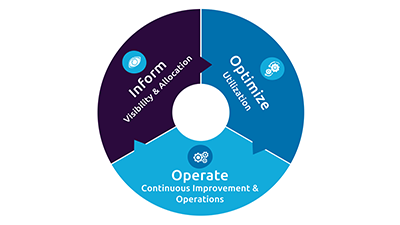

Cover different tech stack needs with efficient management of automated deployments for each type of release. Ensure build, deploy and operate are seamless. Unit / Integration / Security / Performance testing. Infrastructure as a Code and Release Orchestration.

Securing application and infrastructure using compliance checkpoints. Provide central SIEM (Security, Information and Event Management). Cloud compliance and governance. Granular, policy based IAM and authentication controls

Behavioural insight definitions for performance, compliance and security on your services and applications. Automate monitoring, tracing and logging. Connected view of all performance metrics at one place. Pinpoint issues faster and understand why
