 By: John Abhilash / May 20, 2024
By: John Abhilash / May 20, 2024
Building a Security Shield: The 5 Continuous Phases of Sec in DevSecOps
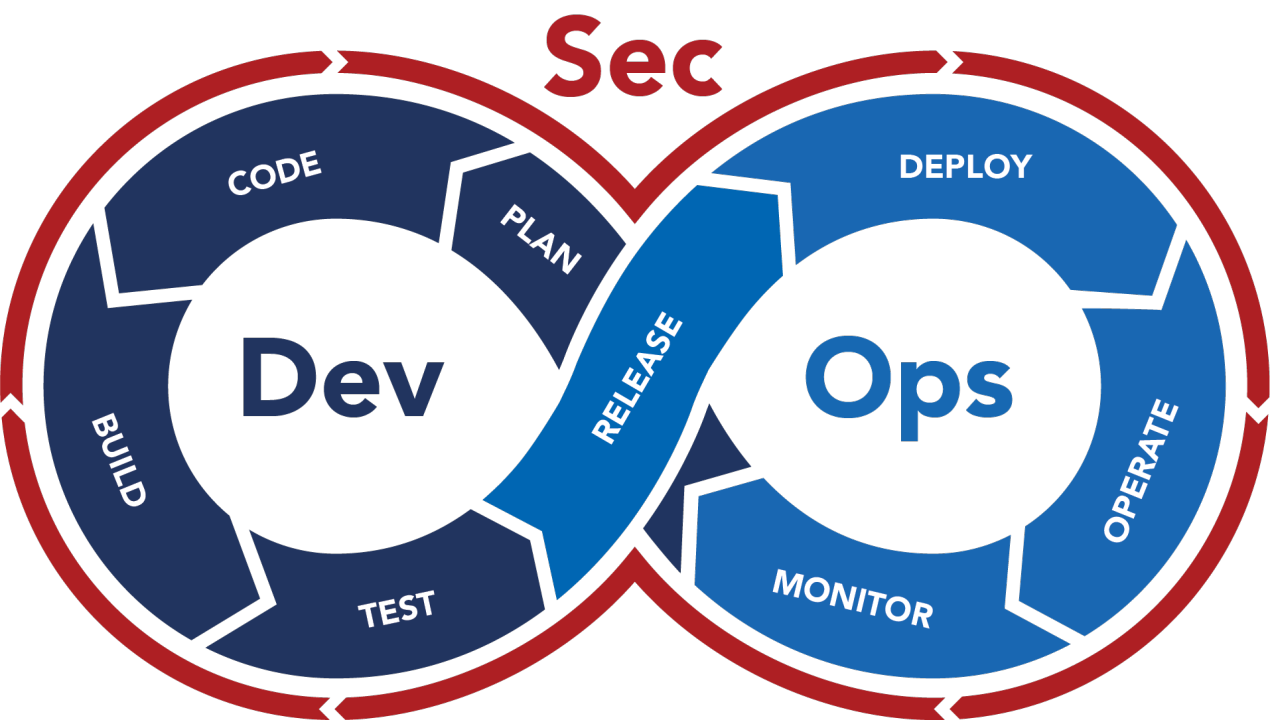
DevSecOps, the marriage of development, security, and operations, has revolutionized software delivery. By integrating security throughout the development lifecycle, DevSecOps fosters faster deployments and more robust applications. However, security within DevSecOps isn’t a linear process; it’s a continuous loop of proactive measures. This blog delves into the 5 circular phases of “Sec” in DevSecOps, highlighting how they work together to create a comprehensive security shield.
Imagine building a house – you wouldn’t start construction without a blueprint, right? Similarly, DevSecOps begins with threat modeling, where potential vulnerabilities are identified and mitigated before code is written. Techniques like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial-of-Service, Elevation of Privilege) help visualize attack vectors and guide security decisions. Tools like OWASP Threat Dragon can be a great starting point.
With the threat landscape mapped, it’s time to scan for existing vulnerabilities. Static Application Security Testing (SAST) tools analyze code for common weaknesses without execution. Software Composition Analysis (SCA) scans dependencies and open-source libraries for known security flaws. These scans provide a vital first line of defense, catching vulnerabilities early in the development process.
Not all vulnerabilities are created equal. The analysis phase involves reviewing scan results, prioritizing risks based on severity and exploitability. Factors like the potential impact of a breach and the ease of exploitation are considered. This prioritization ensures that development teams focus on the most critical issues first, optimizing their security efforts.
Once vulnerabilities are prioritized, it’s time for remediation. Developers fix flaws in their code, update dependencies, or implement workarounds. Security champions can provide guidance and suggest secure coding practices. This phase ensures identified vulnerabilities are addressed before applications move to the next stage.
The DevSecOps cycle is continuous. Even the most secure applications can be compromised by new vulnerabilities discovered after deployment. Security monitoring employs tools and techniques to detect suspicious activity, identify potential breaches, and ensure ongoing system integrity. Solutions like Security Information and Event Management (SIEM) can aggregate logs and identify anomalies.
These five phases – Threat Modeling, Scanning, Analyzing, Remediating, and Monitoring – form a circular loop. Information from each phase informs the others. For example, findings from monitoring may necessitate revisiting threat modeling to address new attack vectors.
DevSecOps thrives on shared responsibility. Developers write secure code, security champions provide expertise, and operations teams maintain secure environments. Communication and collaboration are paramount for a successful DevSecOps implementation.
While the 5 phases provide a strong foundation, additional security considerations enhance DevSecOps:
i)Secure Coding Practices: Training developers in secure coding practices like input validation and proper privilege management significantly reduces vulnerability introduction.
ii)Infrastructure Security: Securing the infrastructure where applications run is crucial. This includes using secure configurations, patching systems regularly, and implementing access controls.
iii)Incident Response: A well-defined incident response plan ensures a swift and coordinated response to security breaches, minimizing damage and downtime.
Building a Culture of Security
DevSecOps is more than just tools and processes; it’s about fostering a culture of security within an organization. By integrating security throughout the development lifecycle, DevSecOps empowers teams to deliver secure applications faster, ultimately building trust with users and stakeholders.
Embrace the Continuous Cycle: The Benefits of DevSecOps Security
The 5 circular phases of Sec in DevSecOps offer a powerful framework for building secure software. By continuously identifying, analyzing, remediating, and monitoring threats, organizations can:
i)Reduce Security Risks: Proactive security measures significantly decrease the likelihood of successful cyberattacks.
ii)Improve Application Quality: Security considerations woven into the development process lead to more robust and reliable applications.
iv)Accelerate Time to Market: DevSecOps eliminates the need for lengthy security audits at the end of the development cycle.
v)Boost Developer Productivity: Automated security tools free up developers to focus on core functionalities.
The ever-evolving threat landscape necessitates continuous improvement, ensuring DevSecOps security practices remain effective. Staying informed about the latest vulnerabilities, attending security conferences, and participating in training programs are all essential for keeping pace with the ever-changing security landscape.
The future of DevSecOps security is bright. Here are some exciting trends to watch:
i)Artificial Intelligence (AI) and Machine Learning (ML): AI and ML can automate security tasks, identify patterns in attack vectors, and predict potential breaches.
ii)Shift-Left Security: Integrating security even earlier in the development process, potentially during the design phase, will further reduce vulnerabilities.
iii)Security as Code (SecCode): Treating security configurations like code allows for version control, automation, and easier collaboration.
By embracing these trends and continuously refining their DevSecOps security practices, organizations can build a strong foundation for secure software development, delivering applications with speed, confidence, and a focus on user trust.
Ready to embark on your DevSecOps security journey? Here are some steps to get started:
i)Assess your current security posture. Identify strengths and weaknesses in your development lifecycle.
ii)Define your DevSecOps security goals. What do you want to achieve?
iii)Educate your team. Train developers, security professionals, and operations teams on DevSecOps principles.
iv)Invest in the right tools. Select tools that automate tasks and integrate seamlessly with your existing workflows.
v)Start small and iterate. Begin with a pilot project and gradually expand your DevSecOps security practices.
Building a robust DevSecOps security framework requires planning, collaboration, and a commitment to continuous improvement. By following these steps and embracing the circular nature of security within DevSecOps, you can create a secure development environment, fostering innovation and delivering applications with confidence.
Guardian: Revolutionizing Application Security
Key Features of Guardian:
1.Shift Left Security : Early Vulnerability Detection
2.Fast Track your VAPT: Gain insights to your application security posture across various assessments (SCA, SAST, DAST, IAC)
3.Security Driven Development : Streamlined Vulnerability Assessment and Penetration Testing(VAPT)
4.Integration with JIRA: Provided a centralized hub for tracking ,prioritizing and managing security issues.
5.AI powered Remediations: Immediate Resolution Guidance
Guardian’s AI delivers immediate resolution guidance upon identifying vulnerabilities, accelerating the remediation process and fostering a culture of proactive security to enhance overall code quality.
In an era where cybersecurity is paramount, Guardian serves as an indispensable ally, safeguarding applications throughout their lifecycle and empowering businesses to navigate the digital landscape with confidence.
Check Out our Other Resources: OpenTofu Vs Terraform

Leave a Comment